It’s 2026, and a remote IT job posting on a freelance platform looks too good to be true. The pay? $5,000 a month. The work? Just coding, testing, and support. No interviews. No contract. Just wire your crypto wallet and start Monday. Thousands of companies have taken the bait. But behind that screen is not a freelancer from Ukraine or the Philippines - it’s a North Korean operative, using AI deepfakes to look you in the eye during a Zoom call, while quietly siphoning money to fund weapons of mass destruction.
How the Scheme Works
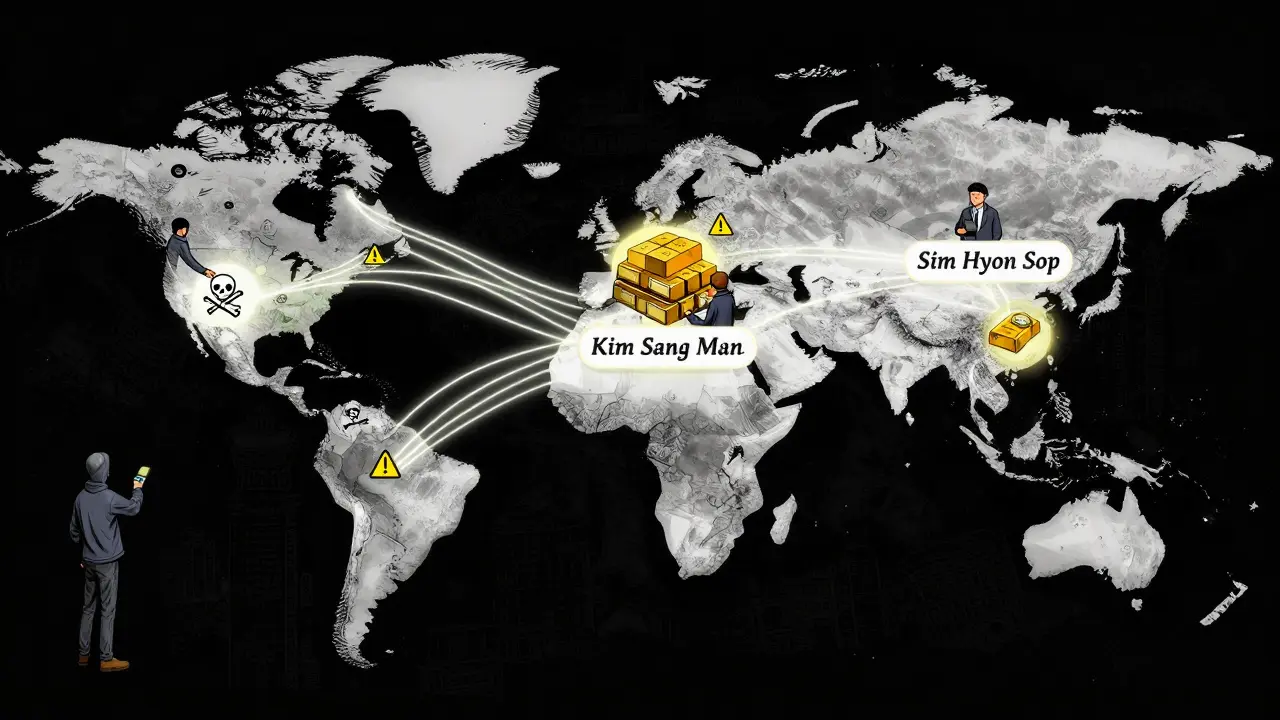
North Korea doesn’t hack exchanges anymore - not primarily, anyway. Instead, it hires its own people as remote workers. These aren’t hackers in hoodies. They’re trained software engineers, cybersecurity specialists, and data analysts, sent overseas under fake identities. They apply for jobs on Upwork, LinkedIn, and niche tech forums. They lie about where they’re from. They use stolen passports, forged diplomas, and AI-generated voices to pass video interviews. Once hired, they demand payment in USDC or USDT - stablecoins that hold steady value and move easily across borders. These workers don’t steal in one big hit. They get paid regularly. $5,000 here. $7,000 there. Monthly. Consistent. The money flows into wallets they control, then gets split across dozens, sometimes hundreds, of other addresses. Each transfer is tiny, scattered, designed to avoid red flags. Eventually, the funds converge in wallets tied to sanctioned North Korean operatives like Kim Sang Man and Sim Hyon Sop. From there, the crypto is converted into cash through over-the-counter (OTC) traders in Russia, the UAE, or China - often using fake businesses or shell companies. This isn’t random crime. It’s state policy. The Multilateral Sanctions Monitoring Team (MSMT) says North Korea made at least $1.65 billion from crypto laundering between January and September 2025 alone. That’s more than $180 million a month. One operation, the $1.4 billion Bybit heist in February 2025, made headlines. But the real money? It’s in the slow drip of payroll payments from unsuspecting companies.Why Stablecoins Are the Weapon of Choice
Bitcoin and Ethereum are too volatile. Too traceable. Too noisy. Stablecoins like USDC and USDT are the perfect tool. They’re pegged to the U.S. dollar. They move fast. They’re accepted everywhere. And because they’re built on blockchains like Ethereum and Tron, they can be shuffled through dozens of wallets before anyone notices. The U.S. Treasury confirmed in June 2025 that North Korean operatives specifically request stablecoins. Why? Because they’re the bridge between crypto and cash. OTC traders - often operating out of Dubai or Moscow - take the stablecoins and give back dollars in cash, bank transfers, or even gold. No KYC. No questions asked. The money disappears into the global financial system, then reappears in North Korea to buy copper for munitions, missile parts, or high-tech surveillance gear. According to the MSMT report from October 2025, these stablecoin transactions are directly linked to military procurement. Copper, lithium, rare earth metals - all bought with crypto laundered through fake IT jobs. This isn’t just money laundering. It’s arms funding.How Companies Get Tricked
Most companies don’t realize they’re hiring a regime-backed operative. The workers appear professional. They’re cheap - often offering rates 20-30% below market. They’re eager. They’ll start immediately. No contract needed. They’ll even work weekends. They use AI tools to fake video calls, sometimes even mimicking your accent or tone. One Canadian tech startup lost $280,000 over six months to an operative who showed up in every Zoom meeting with perfect lighting, perfect English, and a fake degree from MIT. The RCMP’s July 2025 advisory lists the red flags:- Requests for cryptocurrency payments only
- Multiple logins from different countries in one day
- Refusal to sign a contract or provide ID
- Overly low rates compared to peers
- Use of AI-generated photos or voices
The Real Cost to Businesses
The average loss per company? $47,000. That’s according to the Canadian Anti-Fraud Centre’s Q3 2025 report. And 78% of those cases involved crypto payments. Some companies lose less. Others lose millions. The U.S. Department of Justice indicted four North Korean nationals in July 2025 for stealing $900,000 in virtual currency from U.S.-based firms. The names? Joshua Palmer. Alex Hong. Fake identities. Real damage. The worst part? Once the crypto leaves your wallet, it’s gone. No chargebacks. No refunds. The blockchain doesn’t care who you are. Once it’s sent, it’s irreversible.How Governments Are Fighting Back
The U.S., Canada, Japan, South Korea, and 11 other nations are coordinating sanctions. In July 2025, the U.S. Treasury sanctioned Chinyong Information Technology Cooperation Company - the main agency that recruits and deploys these workers. They also went after Vitaliy Sergeyevich Andreyev, Kim Ung Sun, and Korea Sinjin Trading Corporation. All were tied to the laundering pipeline. The FBI and DOJ have seized over $7.7 million in crypto, NFTs, and digital assets linked to these operations. They’ve frozen wallets tied to North Korean operatives. They’ve pressured exchanges to block known DPRK-linked addresses. The Financial Action Task Force (FATF) updated its global guidance in June 2025, telling crypto platforms to watch for patterns: small, regular payments from new users, requests for stablecoins, and inconsistent location data. And there’s new tech coming. FinCEN, the U.S. financial crimes unit, is testing a prototype system expected to launch in early 2026. It can spot DPRK-linked wallet clusters with 89% accuracy by analyzing transaction timing, wallet age, and fund flow patterns.
What Companies Can Do
You don’t need to be a cybersecurity expert to protect yourself. Here’s what works:- Never pay in crypto unless you’re 100% sure of the person. Use payroll platforms with built-in KYC. Pay via bank transfer, not wallet.
- Verify identities with multiple video calls. Ask them to show a government ID, then ask them to spell their name backwards. Deepfakes can’t handle that.
- Check their education and work history. Call the university. Email the former employer. DPRK operatives use fake diplomas 92% of the time.
- Use blockchain analytics tools. Services like Chainalysis or Elliptic can flag if a wallet has ever been tied to North Korea. Run the wallet address before paying.
- Require contracts. If they refuse to sign, walk away.
The Bigger Picture
This isn’t just about fraud. It’s about survival. North Korea’s economy is crushed under sanctions. Its people are starving. But its military isn’t. The regime has turned the global remote work boom - a $427 billion industry - into a weapon. Every time a company hires a fake IT worker, they’re indirectly funding missile tests, nuclear warheads, and cyberattacks on hospitals and power grids. The world is waking up. Governments are acting. Tech tools are improving. But as long as crypto remains anonymous and remote work is easy, the scheme will evolve. Maybe next time, they’ll use NFTs. Or decentralized finance protocols. Or AI-generated freelance profiles that can pass automated screening tools. The only defense? Vigilance. Verification. And never, ever paying someone you’ve never met in crypto.Are North Korean IT workers still active in 2026?
Yes. Despite increased sanctions and better detection tools, North Korean IT workers remain active in 2026. The Multilateral Sanctions Monitoring Team confirmed ongoing operations through September 2025, and U.S. Treasury data shows new wallet clusters tied to DPRK operatives emerging monthly. While the volume may drop due to improved countermeasures, the regime has shown it can adapt quickly - shifting to new platforms, tools, and laundering methods.
Can you trace crypto payments back to North Korea?
Yes, but it’s complex. Blockchain analysis firms like Chainalysis and Elliptic have mapped out hundreds of wallets used by DPRK operatives. These wallets show patterns: small, regular deposits from different countries, rapid movement through mixers or bridges, and eventual consolidation into known sanctioned addresses. While individual transactions are hard to trace, clusters of activity are increasingly detectable. The U.S. FinCEN’s new system, launching in early 2026, can identify DPRK-linked clusters with 89% accuracy.
Why don’t exchanges block these payments?
Many exchanges do - but not all. Major platforms like Coinbase and Binance have blocked known DPRK-linked wallets. But smaller exchanges, especially those based in jurisdictions with weak oversight, still process these transactions. OTC traders - who operate outside exchange systems - are the biggest loophole. They accept crypto from anyone, often without ID, and convert it to cash. That’s why the U.S. Treasury has sanctioned multiple OTC facilitators, including a person known only as ‘Lu’.
Is it illegal to hire a North Korean IT worker unknowingly?
No, not if you truly didn’t know. U.S. and international sanctions target the regime and its enablers, not individual employers who are victims of fraud. However, if you ignore red flags - like crypto-only payments or fake documents - regulators may consider you negligent. In some cases, companies have been fined for failing to conduct basic due diligence. The key is proving you made a good-faith effort to verify the worker.
How can I check if a crypto wallet is linked to North Korea?
Use free blockchain explorers like Etherscan or Tronscan to look up the wallet address. Then cross-check it with public sanctions lists from the U.S. Treasury’s OFAC database or Chainalysis’ React platform. Some cybersecurity firms offer wallet screening tools for businesses. If the wallet has ever received funds from a known DPRK-linked address, or has sent funds to a sanctioned entity, it’s high-risk. Always verify before sending any payment.
What’s the difference between this and the Lazarus Group hacks?
The Lazarus Group steals large sums in single attacks - like the $625 million Harmony Bridge breach in 2022. The IT worker scheme is slower, quieter, and more sustainable. Instead of breaking in once, they get paid monthly like real employees. This avoids triggering alarms. It’s less flashy, but far more reliable. According to Chainalysis, the IT worker scheme generated 43% of North Korea’s crypto revenue in 2025 - more than direct exchange hacks.



Margaret Roberts
January 26 2026This is all fake. The whole thing. The US government just wants you scared so they can track every crypto transaction. They’ve been lying about North Korea since the 90s. You think they don’t control the blockchain too? Of course they do. This is just another psyop to justify surveillance. Wake up.
They’re not even using stablecoins. It’s all centralized. They just want you to think it’s decentralized so you’ll keep using it. The real money is in fiat. Always has been.
And who’s really behind this? The same people who told you 9/11 was an inside job. Same playbook. Same fear. Same lies.
Stop feeding the machine.
They want you paranoid. They want you checking wallets. They want you terrified of a remote worker. Meanwhile, your taxes are going to drones and private prisons. But hey, at least you’re not hiring a North Korean.
They’re not even real people. The whole thing’s AI-generated. Just like this post.
Think for yourself. Or don’t. Either way, they’re watching.
And if you’re reading this? You’ve already been flagged.
Jonny Lindva
January 28 2026Man, this is wild but also so real. I had a guy on Upwork last year who was ‘from Canada’ but his Zoom background kept changing between Tokyo and Berlin. He paid for his own software license with USDT and refused to sign anything. I thought he was just a weird freelancer. Now I’m sweating.
Thanks for the checklist - I’m running every future hire through Chainalysis now. Better safe than sorry.
Also, if you’re hiring remotely, just use PayPal or direct deposit. No crypto unless you’re 100% sure. And even then… maybe don’t.
Jen Allanson
January 29 2026It is profoundly disturbing that any corporation, no matter how well-intentioned, would entertain the notion of remunerating an individual whose labor directly or indirectly funds weapons of mass destruction. This is not a ‘freelance gig’ - it is complicity. The moral failure of modern capitalism is that we have normalized transactional detachment to the point where we no longer ask who benefits from our payments.
Employers are not innocent bystanders. They are enablers. And the fact that so many dismiss this as ‘just business’ reveals the depth of our ethical decay.
There is no such thing as ‘unintentional’ support of a genocidal regime. Ignorance is not an excuse. It is a choice.
Until companies are held legally and morally accountable for the origin of every dollar they disburse, this will continue. And we will all be guilty.
Harshal Parmar
January 31 2026Bro, I’m from India and I’ve seen this kind of stuff up close. We get so many fake profiles on Freelancer.com - people with perfect English, fake degrees from Harvard, always asking for crypto. At first I thought they were just scammers. Now I realize some of them might be state-sponsored.
But here’s the thing - the real problem isn’t North Korea. It’s that companies are too lazy to verify. Why hire someone who won’t sign a contract? Why pay in crypto when you can use Stripe? Why not do a 3-call verification process?
It’s not rocket science. It’s basic HR. We’re so obsessed with speed and cheap labor that we forget to check if the person is even real.
And yeah, I know, ‘But they’re so good at their job!’ - so was the guy who sold me a ‘fake Rolex’ that broke in 2 days.
Don’t be the one who funds a missile with your payroll. Just say no to crypto hires unless you’ve got a forensic accountant on speed dial.
Stay safe, stay smart.
Peace out 🙏
Darrell Cole
February 2 2026This article is full of hype and zero evidence. You cite MSMT and FinCEN like they’re gospel but they’re government agencies with agendas. Where’s the public blockchain evidence? Where are the wallet addresses? Where’s the proof that Kim Sang Man is even real? This reads like a CIA briefing written by a grad student. Also stablecoins aren’t untraceable - they’re the most traceable crypto asset. The real story is how the US is using fear of North Korea to push centralized KYC on DeFi. This isn’t about weapons - it’s about control. And you’re helping them.
Dave Ellender
February 2 2026Interesting read. I’ve worked with remote devs from Eastern Europe and Southeast Asia - the red flags you listed are spot on. One guy I hired asked for USDT, claimed he was ‘in Poland’ but his GitHub commits were at 3am his time and 11am EST. I didn’t think much of it until now.
Good to know what to watch for. I’ll be running all new hires through OFAC now. Simple step, huge difference.
Barbara Rousseau-Osborn
February 3 2026OFAC? LOL. You think the US government is clean? They’ve been laundering money through shell companies for decades. This whole ‘North Korea is hacking your Upwork jobs’ is a distraction. They want you to blame the DPRK so you don’t ask why your CEO makes $20M while you’re on a 1099 with no benefits.
Also, ‘AI deepfakes’? Please. I’ve seen Zoom calls from real people who look worse than deepfakes. Your ‘red flags’ are just ‘people who don’t like paperwork.’
And you say ‘never pay in crypto’ - but what if you’re in a country with no banking? What if your freelancer is in Venezuela? Are they evil too?
You’re not protecting the world. You’re just scared of people who don’t look like you.
🙄